Task: Design an automated solution for infrastructure provisioning, application deployment, and monitoring.
This project demonstrates practical implementation of modern DevOps principles, showcasing a comprehensive workflow from cloud infrastructure provisioning to application deployment and real-time monitoring. It incorporates industry-standard tools and best practices to build an automated, scalable cloud-native environment designed to enhance operational efficiency and system reliability.
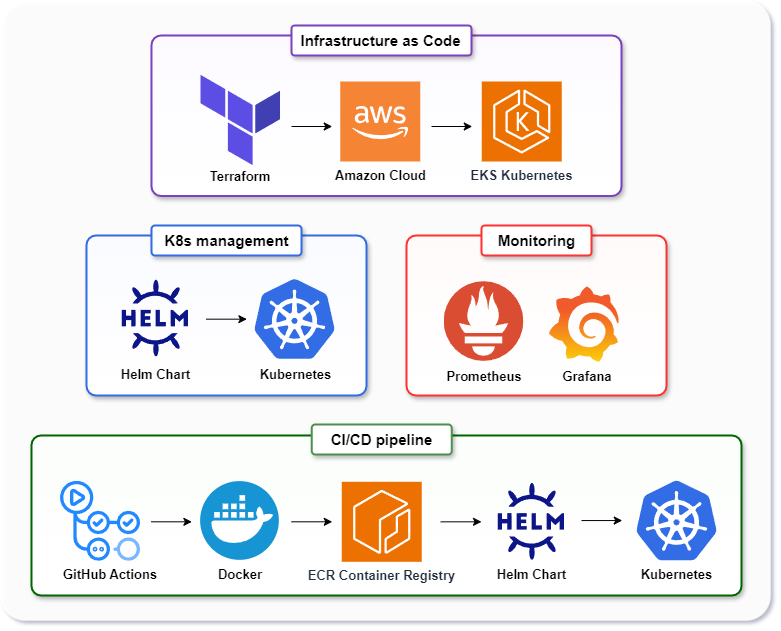
Technology stack
- AWS: Cloud infrastructure provider
- Terraform: Infrastructure as Code (IaC)
- Helm: Kubernetes deployment management
- GitHub Actions: CI/CD automation
- Prometheus & Grafana: Monitoring & visualization
Cloud-Native DevOps Pipeline
Best practices followed
-
Containerization for environment consistency
- Docker-based containers ensure identical environments across development, testing, and production stages.
- Impact: Eliminates inconsistencies across environments and simplifies cross-stage deployment.
-
Proactive monitoring with Prometheus and Grafana
- Prometheus collects system and application metrics; Grafana enables real-time dashboard visualization.
- Outcome: Early issue detection, performance optimization, and improved system resilience.
-
Separation of infrastructure and application logic
- Infrastructure provisioning (Terraform) and application deployment logic (Helm charts) are maintained in isolated codebases.
- Advantages: Supports modular updates, minimizes interdependencies, and enables independent management of infrastructure and application lifecycles.
-
Scalable architecture with horizontal scaling
- Kubernetes auto-scaling and cloud-native resources enable the application to scale horizontally based on demand.
- Impact: Optimal resource utilization and consistent performance under variable workloads.
-
Version control for infrastructure and application code
- All Terraform configurations, Helm charts, and application code are versioned in GitHub using Git.
- Benefits: Enables precise tracking of changes, fosters team collaboration, and provides instant rollback capabilities to stable states.
Areas for improvement
-
Automated testing for Kubernetes configurations
Introducing automated testing for Kubernetes configurations validates Helm charts early in the development cycle, ensuring reliable, error-free deployments.
-
Enhanced security practices
Strengthening security through fine-grained IAM roles, encrypted secret management (e.g., AWS Secrets Manager), and strict access controls reduces security risks and enhances system integrity.
-
Automated rollbacks and safe deployments
Implementing rollback mechanisms in the CI/CD pipeline ensures rapid recovery from failed deployments, minimizes downtime, and reduces manual intervention.